5/25/2018
Australia: Final Report Issued On Redflex Speed Camera HackSpeed camera commissioner issues final report in the hacking of Redflex speed cameras in Victoria, Australia.
The government official responsible for maintaining public confidence in photo enforcement on Thursday released the results of his investigation into last year's hacking of speed cameras in Victoria, Australia. Speed camera commissioner John Voyage identified a number of problems with the way Redflex Traffic Systems and the state government handled the scandal.
Police Minister Lisa Neville had no idea that dozens of automated ticketing machines had been infected with the WannaCry virus until 3AW Radio host Neil Mitchell called to ask her for comment on June 22, 2017. Neville was furious at Redflex for failing to notify her of the speed camera infection on June 6.
"They came to be infected because the security to the computer network was breached, due to insufficient security measures and an inadequate adherence to set practices," the report concluded.
Voyage found that, despite having Neville's full support, officials attempted to stonewall his inquiry.
"I had expected this request from the minister would be understood to mean that every relevant document, fact or item would be handed up and volunteered in a collaborative spirit," Voyage explained. "However what gradually occurred over the months of this investigation seemed consistent with a widespread culture within the relevant parts of the department (and in particular [the speed camera program]) of declining to supply relevant information unless it was specifically nominated. There lies the difficulty in this investigation."
Voyage asked for one of the infected hard drives as well as copies of all relevant documents and emails related to the incident. Despite receiving 10,000 pages of documents four months after his request, Voyage noted the emails provided were "selective" and in a format that made searching difficult. The information that he did receive shed new light on what happened.
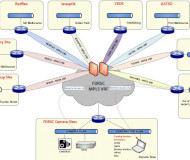
Initially, 102 speed cameras were infected within 48 hours, not 55 infected over the course of two weeks, as officials initially reported. The infection spread over the network, not a USB drive, beginning with the automated ticketing machine at Nicholson Street and Victoria Parade in East Melbourne.
"The current design of the [speed camera] network lacks appropriate security," the report found. "Some of the systems were infected with malware due to vulnerable operating systems that did not have critical patches applied. This infection and subsequent spread was assisted by poor network topology and security design."
The WannaCry malware takes advantage of a set of leaked tools from the US National Security Agency that are used to compromise computers using older operating systems. As soon as a WannaCry file is loaded onto a vulnerable machine, it begins encrypting data files stored locally and any connected network. The malware then demands a $300 ransom, paid in bitcoin, to unlock the files.
Getting the speed cameras back online so they could continue issuing tickets was the top priority for the Victorian government. Last year, the devices generated $193 million in net profit. Voyage concluded that the cameras are now reliable. He recommended the speed camera program install the latest security patches and use a firewall to prevent future malware infections.
A copy of the report is available in a 6mb PDF file at the source link below.


